The Firewall Era Is Dead. Long Live the Algorithm.
You know the old saying: generals always fight the last war. Cybersecurity leaders do the same thing. They build taller walls, thicker firewalls, and shinier access controls—believing the enemy is still outside, battering the gates.
But here’s the problem: the gates aren’t even where the war is happening anymore.
The real action is happening deep inside, in the models we’ve decided to trust. AI and machine learning aren’t side tools anymore—they’re running the show. They decide which transactions are fraud, which resumes get read, which emails you never see, and which “anomalies” your SOC ignores. In other words, the defenses have become the battlefield.
And here’s the twist nobody wants to admit: the thing we’re leaning on to protect us can be turned against us faster than you can say “zero trust.”
The Enemy Has Your Gate Badge
Once upon a time, hacking meant brute-forcing a password or sneaking through a firewall misconfiguration. Now? A bad actor doesn’t need to get through your network perimeter if they can poison the training data of the model that decides what “normal” looks like.
Think about it:
Change a handful of pixels, and a model can mistake a tank for a turtle.
Slip in some tainted rows of training data, and suddenly your fraud detection system thinks fraud is just good customer service.
Drop in a carefully crafted prompt, and your large language model politely hands over your crown jewels while smiling.
This isn’t science fiction. It’s already happening. The enemy isn’t trying to storm your castle—they’re bribing the guard.
Data: The New Zero Day
In the old world, the scariest thing was a zero day—a bug nobody knew about yet. In the new world, the real zero day lives inside the data pipeline.
If I can slip bad data into your model before it’s trained—or during retraining—you’ll never even know. Your entire system will confidently make the wrong decision, over and over, with a big shiny probability score to make everyone feel safe.
And executives? They eat that stuff up. A dashboard with a confidence interval looks so official. Nobody wants to be the one to say, “Hey, maybe the oracle is drunk.”
But that’s exactly what’s happening. Garbage in, garbage out… except this garbage comes wrapped in statistical authority.
Explainability Theater
Vendors know people are nervous, so they sell “explainable AI.” Nice charts. Pretty arrows. Reasons like “education fit” or “geolocation risk.”
Let’s be honest: most of this is marketing theater. It’s like a politician explaining why they voted for a bill they never actually read. It soothes the room. It doesn’t mean the decision was right.
And attackers don’t care about your pie charts. They care that your system will keep rubber-stamping their activity because they’ve tricked your oracle into believing up is down.
Governance Just Got Sexy
“Governance” used to be the dullest word in the room. Committees, binders, PowerPoint slides with flowcharts. Snooze.
But in the AI age? Governance is the new rock star.
It’s not about rules for rules’ sake. It’s about circuit breakers. Who trained the model? What data was used? Is there a record of retraining? Did anyone actually test it against adversarial attacks?
Here’s the uncomfortable part: AI isn’t software. It doesn’t run like code. It guesses. It predicts. It adapts. When it goes wrong, you can’t just patch it—you need to retrain it, and retraining means owning up to your blind spots.
Which is precisely why most companies avoid the conversation. Humility is not exactly a line item in the quarterly report.
History Keeps Slapping Us in the Face
We’ve done this dance before.
The Cold War wasn’t just nukes—it was misinformation and propaganda.
The 2008 financial crash wasn’t a liquidity crisis—it was blind trust in risk models nobody understood.
Enron didn’t implode because people stopped buying energy—it collapsed because the numbers were massaged until everyone believed the fairy tale.
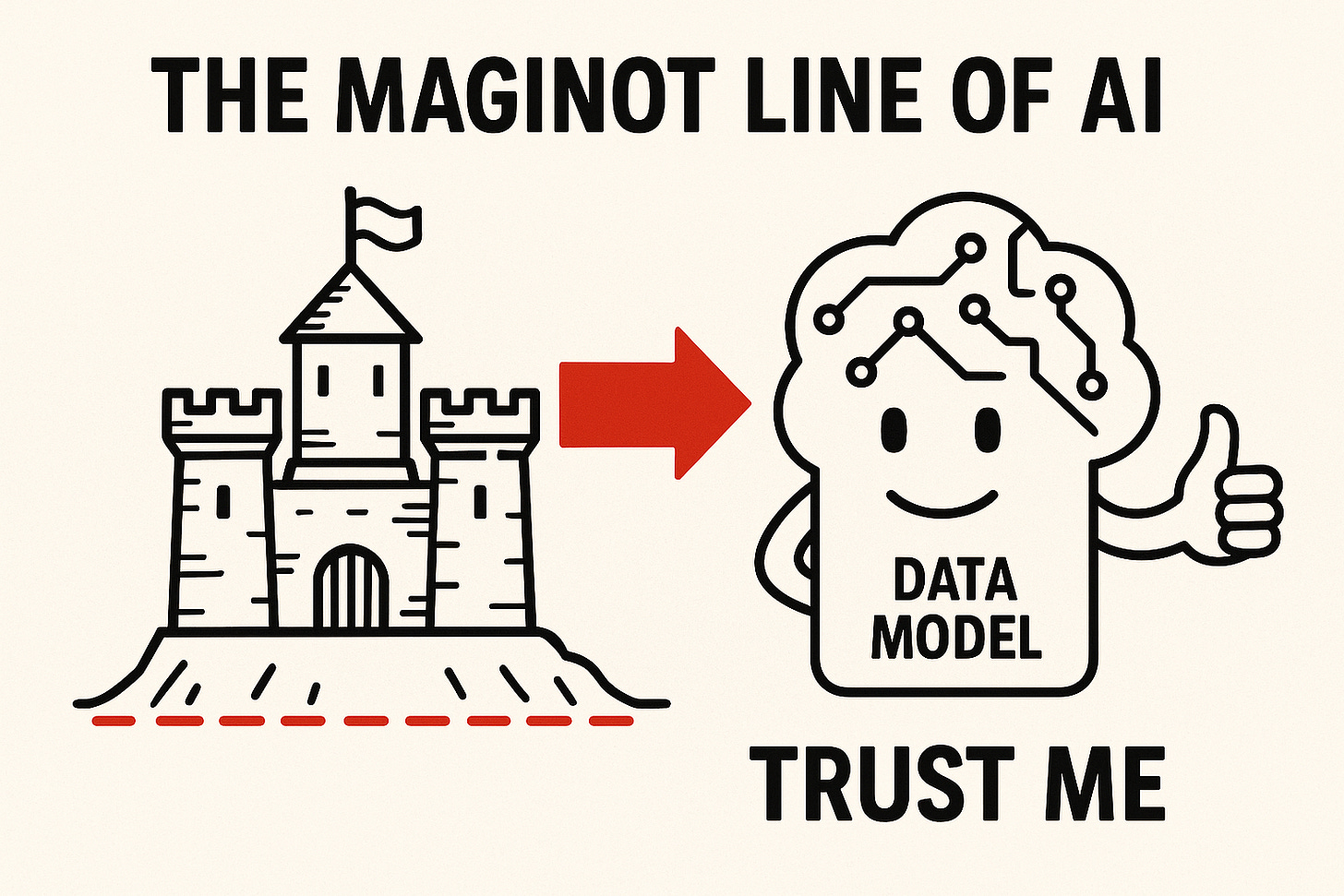
Every era has its Maginot Line: a defense we thought was impenetrable until it wasn’t.
Today’s Maginot Line is the AI model. And like all the others, it will fail if we keep outsourcing judgment without accountability.
Regulators With Old Maps
Governments are scrambling to catch up. The EU’s AI Act, U.S. executive orders, state-level bills—they’re all well-intentioned. But by the time regulations hit paper, models have already moved on.
The danger is that governance devolves into a checklist: did you buy the certification, slap the compliance sticker on the box, and move on? Meanwhile, attackers are laughing all the way to the exfiltration server.
It’s the same old story: laws playing catch-up while adversaries speed ahead.
What To Do About It—Right Now
If you’re in the boardroom, don’t kid yourself: the next breach won’t be a firewall patch you missed. It’ll be your most trusted model betraying you.
Here’s what needs to change:
Secure the Data Pipeline.
Treat data like code. Audit it, test it, version it. Assume attackers are already trying to sneak poison into it.Adversarial Testing Is a Must.
If your AI vendor can’t show you how they hold up against adversarial examples, you’re buying snake oil.Real Auditability, Not Theater.
Forget the pretty dashboards. Demand raw logs, provenance trails, retraining documentation.Build Circuit Breakers.
Don’t let one model’s decision ripple unchecked. One bad prediction should not sink the ship.Humans Stay in the Loop.
The most dangerous phrase in cybersecurity today? “The model says it’s fine.”
The Psychology of Blind Trust
Here’s the part most people miss: the real vulnerability isn’t even technical. It’s psychological.
We love shiny dashboards. Executives drool over “confidence scores.” If it looks official, we believe it. Meanwhile, the one junior analyst waving their hand saying, “This doesn’t look right”? They get ignored.
Attackers know this. They don’t just hack code; they hack human belief. Trick the model into blessing malicious activity, and the humans will happily follow along.
The Punchline
The Maginot Line didn’t fail because it was weak. It failed because it was built for the wrong war.
We’re making the same mistake with AI. Firewalls, identity, zero trust—they matter, but they’re not enough. The battlefield has moved inside the models.
The only real strategy left is ruthless skepticism. Don’t trust the model until it’s proven. Then keep verifying, every single day.
Because the next time your system gets breached, it won’t be knocking at the door. It’ll already be sitting in the control room, flashing a green light, and whispering: “All clear.”
#AI #Cybersecurity #MachineLearning #DataGovernance #RiskManagement #AdversarialAI #TrustButVerify #FutureOfSecurity #EnterpriseLeadership